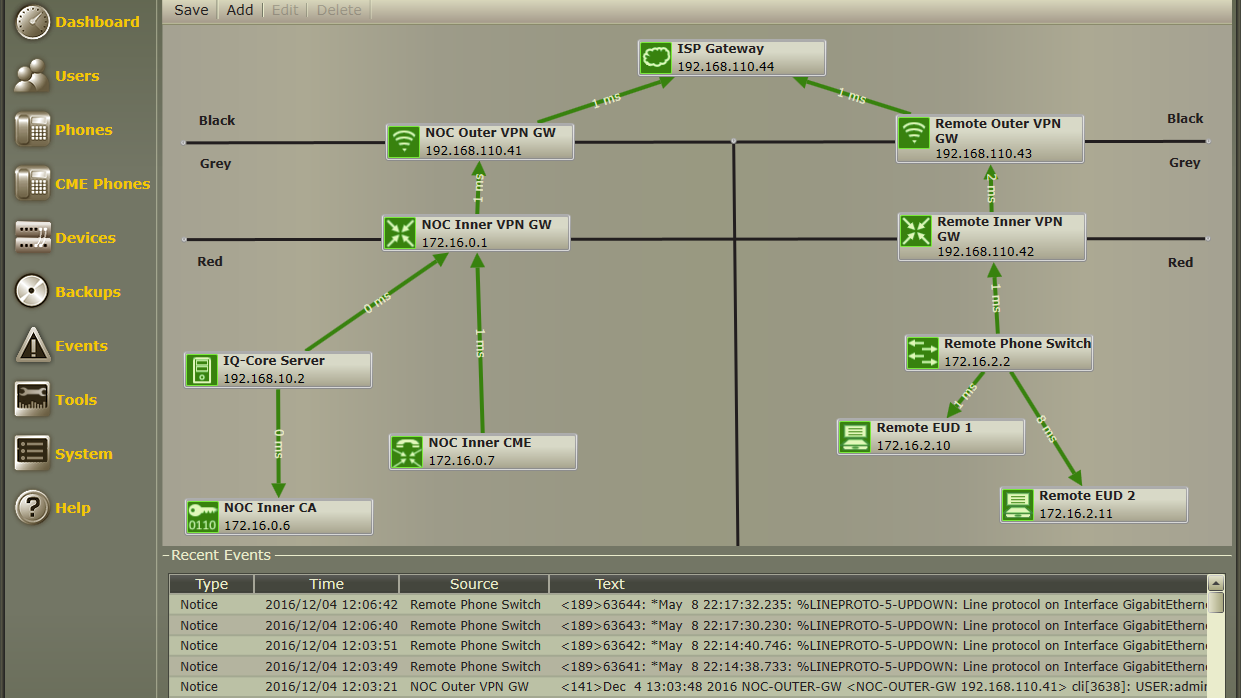
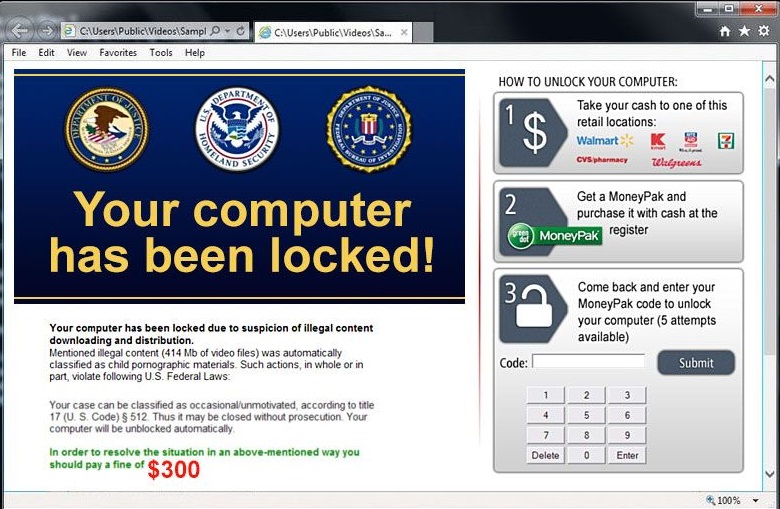
The Big Hack: What are the Implications for Oregonians?
Note: The following post originally appeared on the Cyber Oregon blog here. The world of cybersecurity is full of unexpected surprises and attacks that are ...
Read More Cyber security summer camp looks to fill thousands of jobs | KGW.com
PDX Cyber Camp 2017 a smashing success! Three locations, 65 students, amazingly talented instructors and 15 industry guest speakers from companies like PacStar, Galois, IBM, ...
Read More PacStar & Aruba receive NSA-certification for its tactical server with security software
I'm thrilled to have played a part in making this successful partnership happen with Aruba and PacStar, and shepherding this process through from start to ...
Read More C4ISRNet: Testing of comms management tool shows positive results
Insightful and positive article by Adam Stone, in C4ISRnet. Glad to be a part of it! In independent third-party testing, sponsored by PacStar, researchers found ...
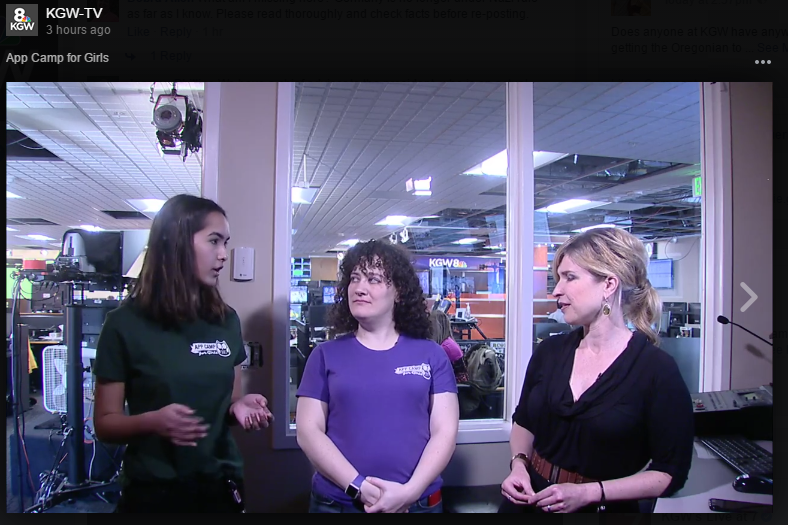
Read More PDX Cyber Camp 2017 on TV!
Check out camp co-founder Amelia Kawasaki discussing AppCamp4Girls and PDX Cyber Camp 2017 on KGW-TV today. First she did a live TV segment (below), ...
Read More U.S. Army’s Deployed WIN-T Program Software Reduces System Management Complexity | SIGNAL Magazine
A communications network management software solution deployed last year across the U.S. Army has proven to drastically reduce network downtime as soldiers operate in an ...
Read More Portland tech executive on escaping the devastation of internment – Portland Business Journal
Credit: U.S. National Achives. Manzanar, California. Dust storm at this War Relocation Authority center where evacuees of Japanese ancestry are spending the duration. (ARC 539961) ...
Read More CYBERSLEUTHING: A PEEK AT OREGON’S NEW SECURITY BREACH DATABASE
I worked with Oregon Business Magazine to create this article, assisting them in research and helping explain possible causes for some recent attacks on Oregon ...
Read More Talk Tech To Me I Cyber Security | Technology Association of Oregon
I'm tickled with how well this TAO podcast came together! Technology Association of Oregon Executive Skip Newberry made this easy, and the editing team really ...
Read More Speaking at Remote Monitoring and Control Conference 2016
I'm a speaker at the Remote Monitoring & Control conference, Nov 4th, 1:30pm. My talk is titled "Applying Military Tactical Networking Lessons-Learned to Enable Industrial ...
Read More